What is a matching sheet?
A matching sheet, or a matching quiz, is a sheet with two columns. In the first column there will be a word, statement or question, and in the second column are the answers, jumbled around in a different order.
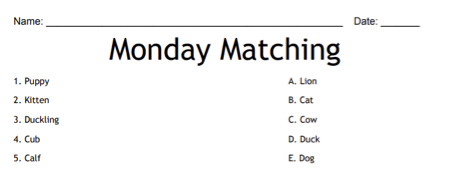
Students will then match the items in column A with the related answers in column B. Here is an example of a simple matching sheet where students would match up the name of the baby animal in column A with the adult name of the same animal in column B:
Who can play matching sheets?
Matching sheets are so customisable that teachers can create matching quizzes for any different age and education level. Your matching test template can be as simple as single word associations, or as complicated as difficult equations to solve.
With over 8,000 pre-made matching quiz templates available on WordMint, you can select and customise one of the existing templates or start fresh and create your own.
How do I create a matching worksheet template?
Simply log in to your WordMint account and use our template builders to create your own custom matching quiz templates. You can write your own titles, and then create your question and answers.
For easily adding multiple lines of questions and answers at once, you can use the ‘add multiple clues’ option where you can create all of your matching sheet lines at one time.
What is WordMint?
WordMint is your go to website for creating quick and easy templates for word searches, crosswords, matching sheets, bingo and countless other puzzles. With over 500,000 pre-made puzzles, you can select one of our existing templates, or create your own.
Do you have printable matching quiz templates?
Absolutely! All of our templates can be exported into Microsoft Word to easily print, or you can save your work as a PDF to print for the entire class. Your puzzles get saved into your account for easy access and printing in the future, so you don’t need to worry about saving them at work or at home!
Do you have matching sheet templates in other languages?
Yes! We have full support for matching quiz templates in Spanish, French and Japanese with diacritics including over 100,000 images. You can use other languages just for your titles and instructions, or create an entire matching worksheet in another language. Matching sheets can be a fantastic tool for students learning new languages!
Can I convert my matching quiz template into other puzzles?
With WordMint you can create a template and then use it to convert into a variety of other executions - word search, word scramble, crosswords or many more.
Are matching sheets good for kids?
The teachers that use WordMint love that they are able to create matching quiz templates that challenge their students cognitive abilities, and test their comprehension in a new and interesting way.
You can theme your matching sheet, and the ability to use different languages means that you can work language learning into your lessons as well. Because WordMint templates are totally custom, you can create a matching quiz for kids that suits their age and education level.








